Related Posts
Threat Advisory
Jun 2025
21 November 2022 Published at 14.00
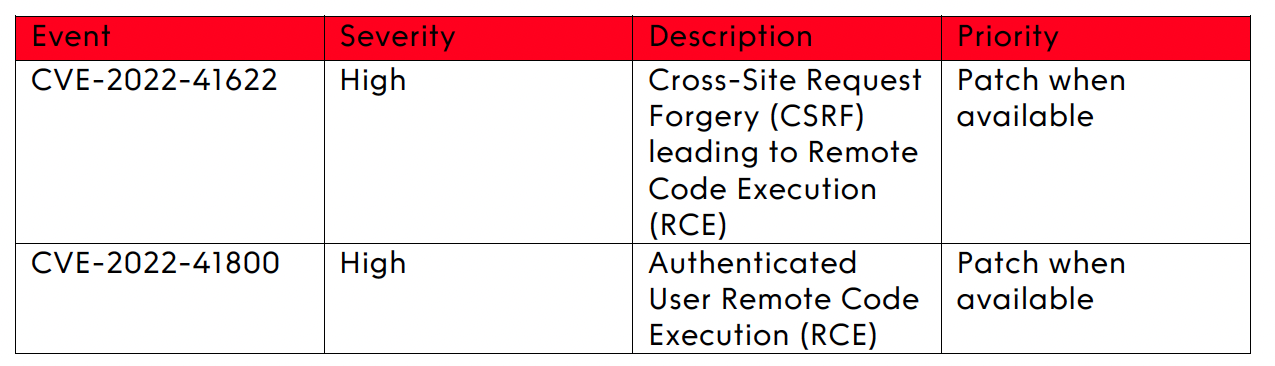
F5 have confirmed that they are aware of two high severity vulnerabilities impacting BIG-IP & BIG-IQ appliances, that may allow an attacker to gain control of these devices remotely, with full root level privileges.
CVE-2022-41622 relates to a vulnerability that permits cross-site request forgery (CSRF) attacks through the iControl SOAP. This is due to a specific iControl .cgi script set to execute with root level permissions, regardless of whether the requestor is authenticated, allowing Remote Code Execution (RCE) to be performed.
Proof of Concept (PoC) exploits for CVE-2022-41622 are available online, but there are currently no reports of this being exploited in the wild.
CVE-2022-41800 relates to a vulnerability whereby an authenticated & sufficiently privileged user can bypass Application Mode controls utilising an undisclosed iControl REST Endpoint, allowing an attacker to cross security boundaries.
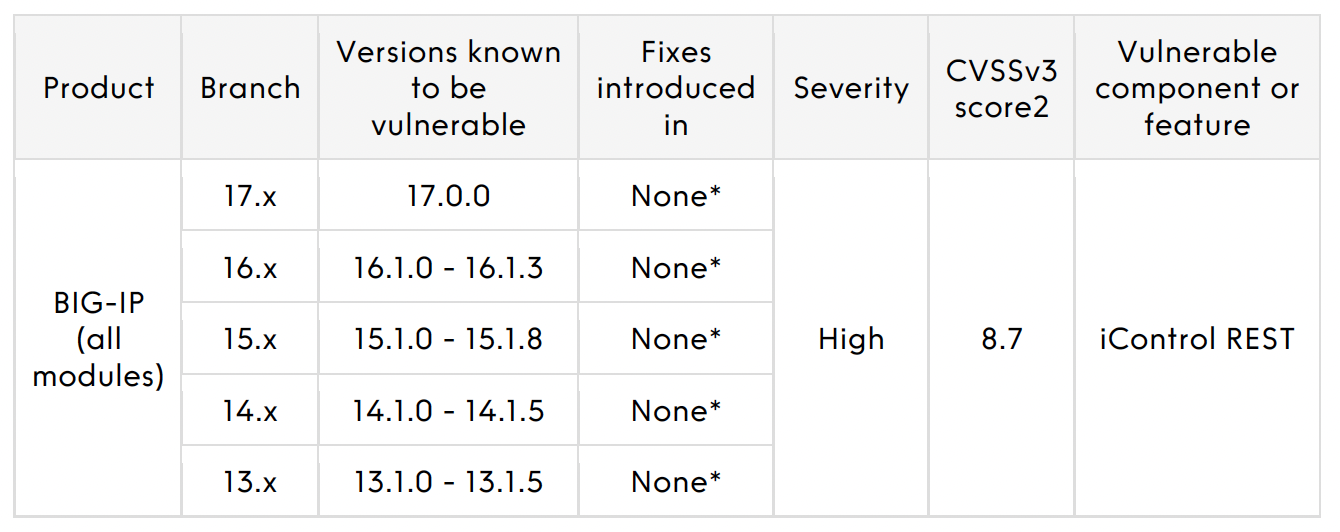
* An engineering hotfix is available for supported versions of BIG-IP. Customers impacted by this issue can request a hotfix from F5 Support.
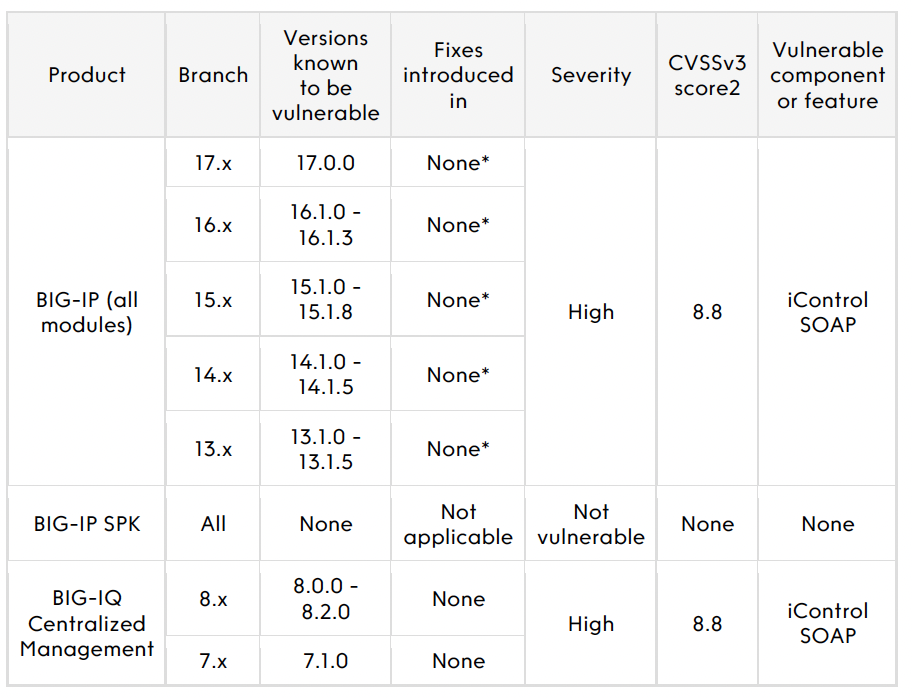
* An engineering hotfix is available for supported versions of BIG-IP. Customers impacted by this issue can request a hotfix from F5 Support. Customers must also disable Basic Authentication for iControl SOAP.
Organisations who have F5 BIG-IP and/or BIG-IQ appliances not currently logging to Splunk should seek to do so at the earliest available opportunity.
Organisations should also contact F5 support to obtain the engineering hotfixes for their appliances.
Organisations who are unable to deploy these engineering hotfixes should follow vendor-recommended mitigations:
If you are unsure if your organisation may be affected by this vulnerability please contact the Adarma team on help@adarma.com and one of our experts will be in touch.
An error has occurred, please try again later.An error has occurred, please try again later.

