NEWS
February 16, 2023
Nvidia users targeted by malware hidden in fake adverts for drivers
Cian Heasley, security consultant at Adarma, shares his views on the TechMonitor article around the malvertising campaign on Google Search, targeting Nvidia.
A malware that targets cryptocurrency wallets is being deployed through fake Nvidia ads on Google’s search portal. This is part of a malvertising boom that shows no signs of slowing down, and analysts are urging users to exercise extreme caution when downloading files.
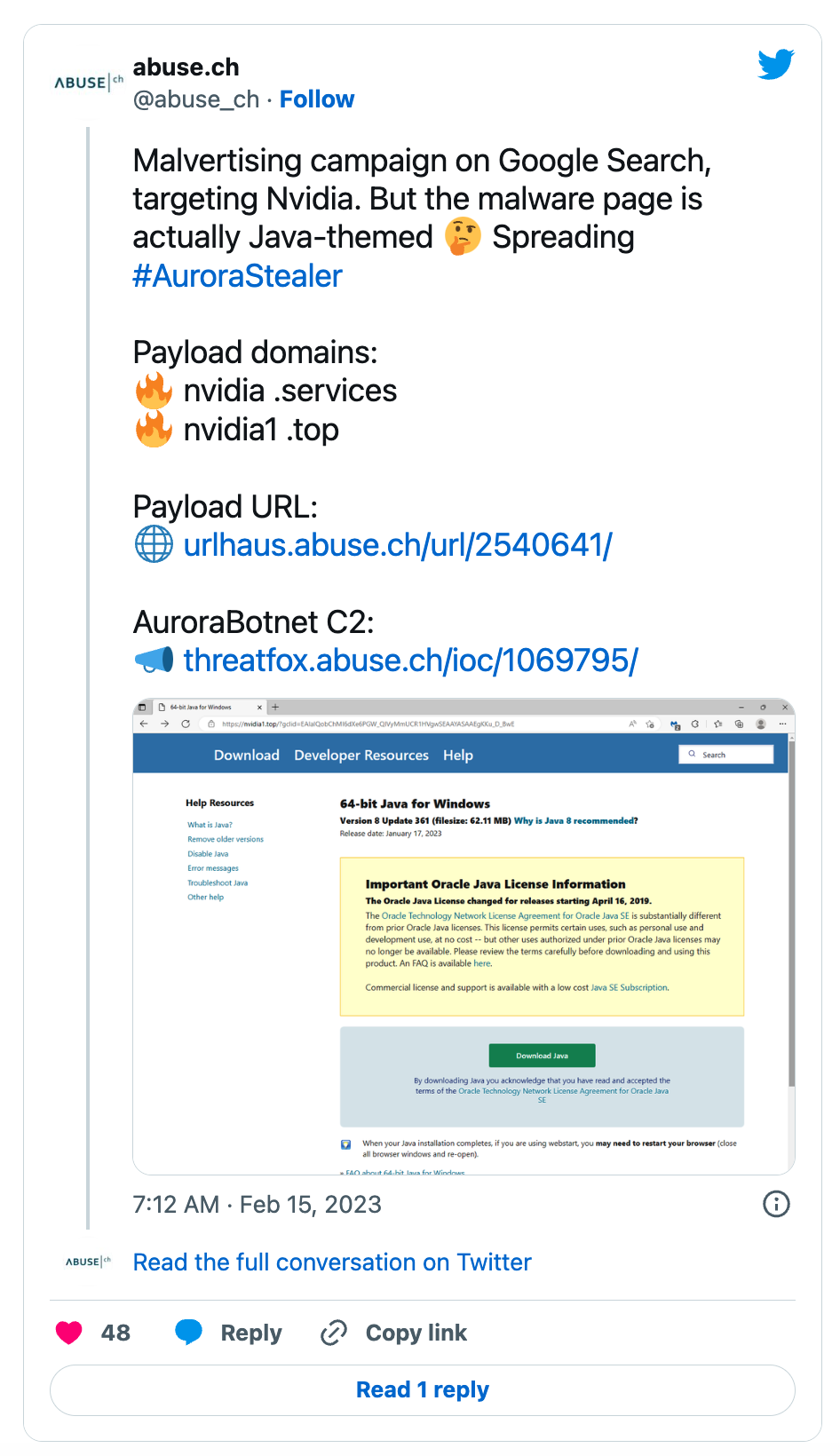
The information-stealing malware, called AuroraStealer, has been found embedded in spoof Nvidia websites that sell drivers for the company’s processors. Spotted by anti-malware platform abuse.ch, the payload domains appear to have been found in links like nvidia.services and nvidia1.top.
Nvidia users targeted through Google Ads in malvertising campaign
The campaign appears to be directing victims to the nefarious websites via Google search adverts.
Aurora infostealer began life as a botnet, but since September 2022 it has been advertised as an infostealer. The malware has been spotted more commonly in the wild over the past six months.
It targets multiple web browsers, as well as browser extensions including those managing cryptocurrency wallets to collect information, according to a report released by security company Sekoia.
“Sold at a high price on marketplaces, collected data is of particular interest to cyber criminals allowing them to carry out lucrative campaigns,” explains the report. “As multiple threat actors, including traffers teams, added the malware to their arsenal, Aurora Stealer is becoming a prominent threat. Cybercriminal threat actors widely distribute it using multiple infection chains including phishing websites masquerading legitimate ones,” states the report.
The fact that criminals using Aurora are targeting Nvidia shows that cybercriminals are changing the way they approach targets, says Javaad Malick, lead security awareness advocate at KnowBe4. “The fact that the criminals are using Nvidia indicates that they want to narrow down a specific type of user or Windows machine,” he says.
Working on specific hardware could enable criminals to spread their malware more widely, adds Chris Hauk, privacy advocate at Pixel Privacy. “Nvidia graphics cards are popular with gamers, which means that even if a small number of Nvidia users fall for the scam, a large number of PCs will be infected, which could possibly pass the malware infection on to other users’ PCs,” he says.
Malvertising itself is nothing new, notes Cian Heasley, security consultant at Adarma, but attacks are becoming increasingly complex, meaning it poses a greater threat to enterprise networks. “Malvertising isn’t a new threat, but the uptick in sophistication of payload has seen a resurgence in its popularity,” he adds. “Malvertising attacks in an enterprise setting can grant threat actors a sneaky entry point to the organisation’s network, from where they can then launch a more devastating attack.”
How to mitigate against malvertising
Recent campaigns appear to be targeting open source and free and niche software for specialist purposes, Heasley says. However, “that these threat actors are now targeting hardware companies shows that the scope of potential threats is growing and that they may have now exploited the obvious options for brand impersonation or malicious fake download sites,” he adds.
Several companies have been impersonated within the current malvertising wave. Free software for remote teams, such as AnyDesk, has proved a common target.
To try to mitigate against this, users could put into practice basic security procedures that should enhance their protection, said Heasley. “To address the problem there needs to be a greater emphasis on verifying the identities of the people claiming to represent companies,” he says. “Checking the backgrounds as to the provenance of the domains being linked to, determining how long these domains have been in existence, who registered the domain, and seeing if the domain’s reputational score is good or bad would be basic steps to take in weeding out malicious ads from true ads by the platforms hosting these advertisements.”
Google could also play its part, notes Hauk. “Google needs to continue to ramp up its advertiser verification process to detect and prevent scams like these,” he argues. “They also need to make the “Ad” notice in ads much larger, in order to make it easier for users to detect adverts.”
![adarma_logo_twgt-black[11615449]](https://adarma.com/wp-content/uploads/2022/10/adarma_logo_twgt-black11615449.png)