Socket is our advanced security operations platform providing managed security services, including managed detection and response, to FTSE 350 customers.
Socket empowers you to manage threat coverage, reduce exposure, and swiftly detect, investigate, and respond to threats at scale.
Distinguished by its open architecture, Socket integrates with your existing security tools and provides additional technical capabilities to support proactive, threat-led risk reduction, tailored to your business needs.
With Socket you can harness our portfolio of interoperable services, organised into areas of SOC capability: threat intelligence, exposure management and detection and response.
Our flexible and modular approach means we can integrate our services seamlessly with your existing operation, helping to achieve a better return on your security investments.
Socket Platform Architecture
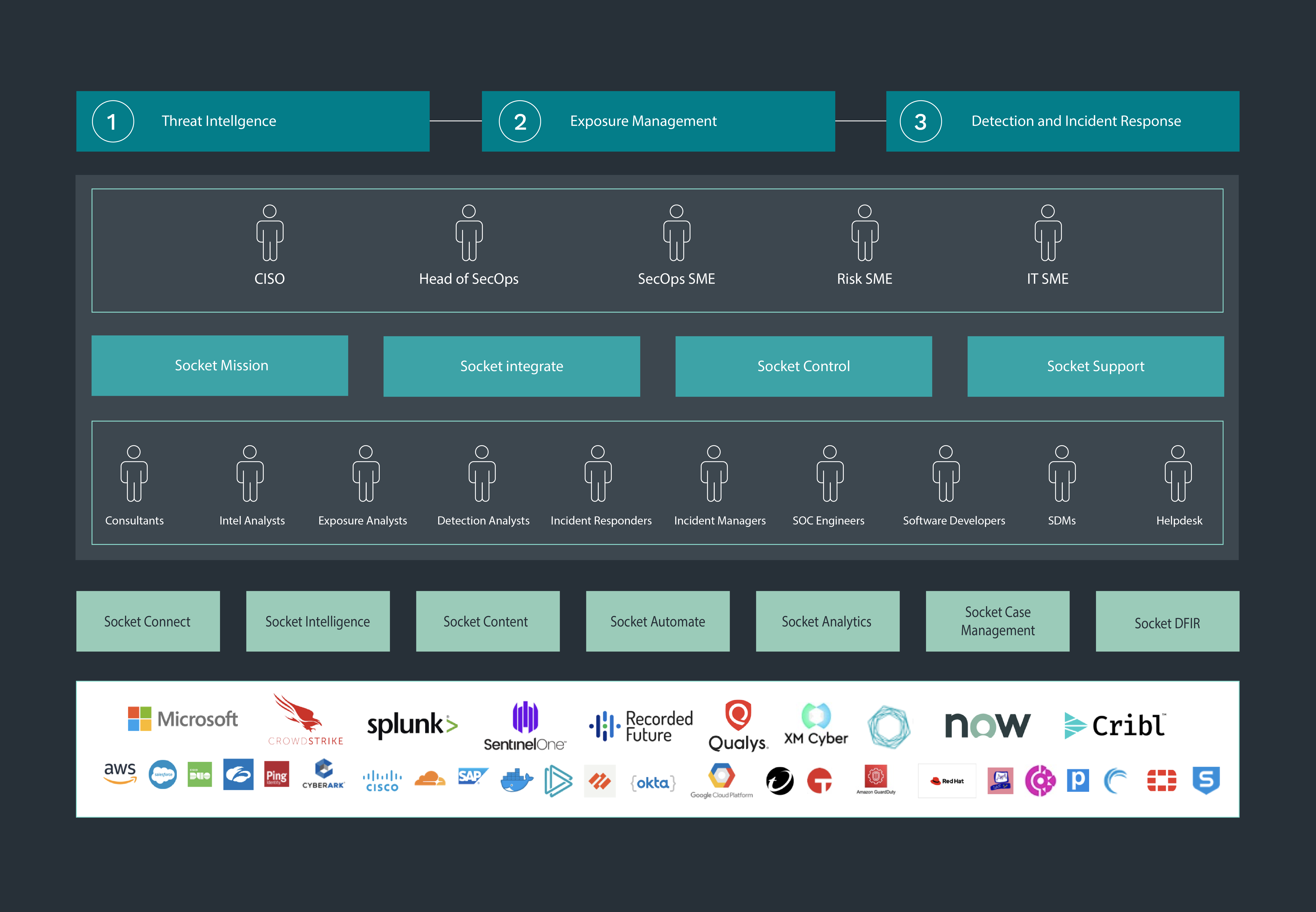
Deliver the Mission
Socket features a rich visual interface that empowers you to define critical assets and services,
prioritise potential threat scenarios, assess threat coverage, and dynamically adapt security measures
to reduce overall risk. Helping to deliver your mission.
Access relevant, curated intelligence linked to your business. Quickly view and assess your cyber risk landscape.
Measure your detection coverage against high-priority threat scenarios, such as ransomware.
Choose additional detections to extend your coverage where you need it most.
Socket allows you to link what threatens you with your organisation’s risk appetite, security controls, and desired security outcomes.
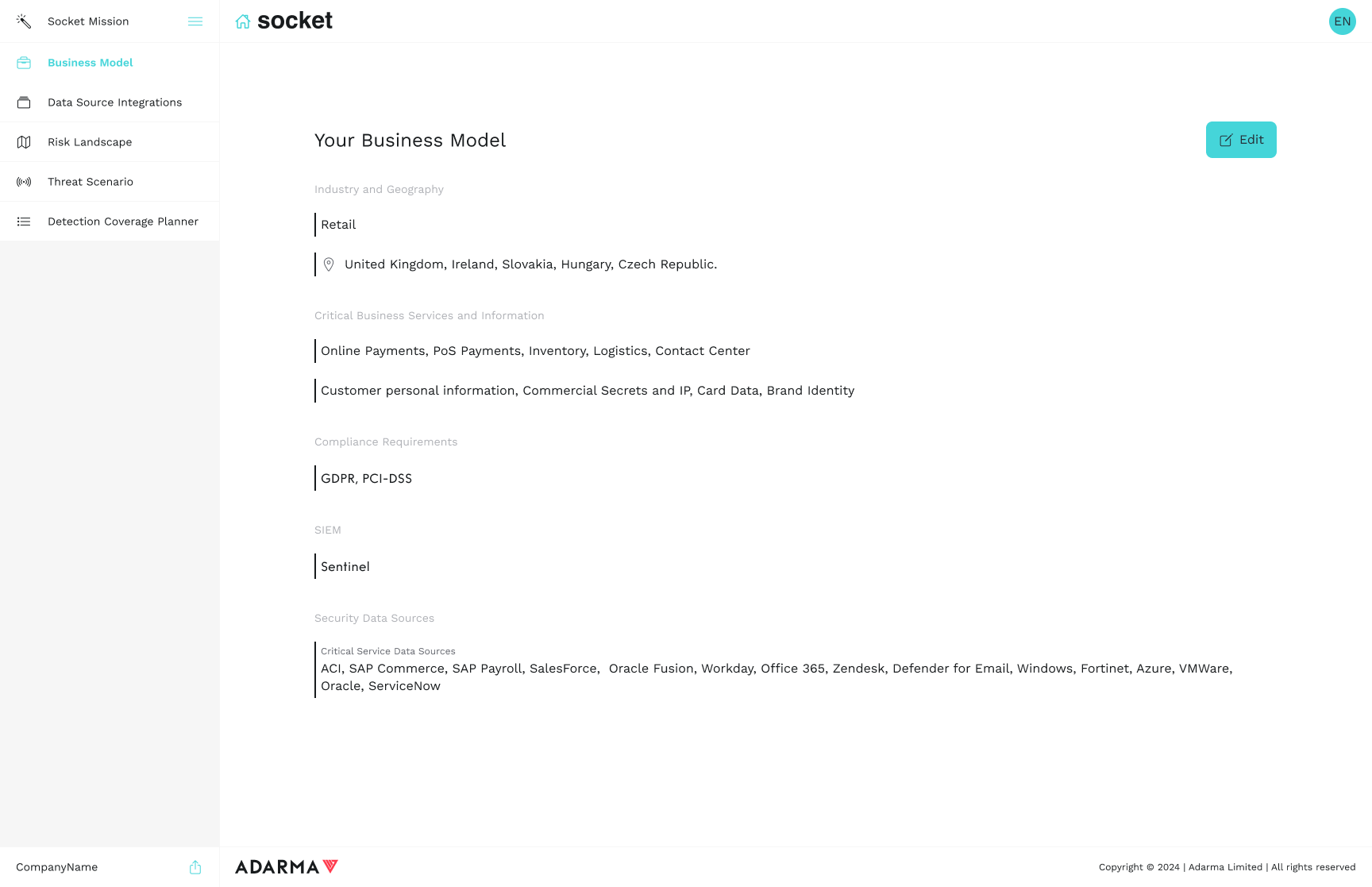
Define the Mission
We start by defining your business model, critical assets and services.
Outcome
Understand what the service seeks to protect and why.
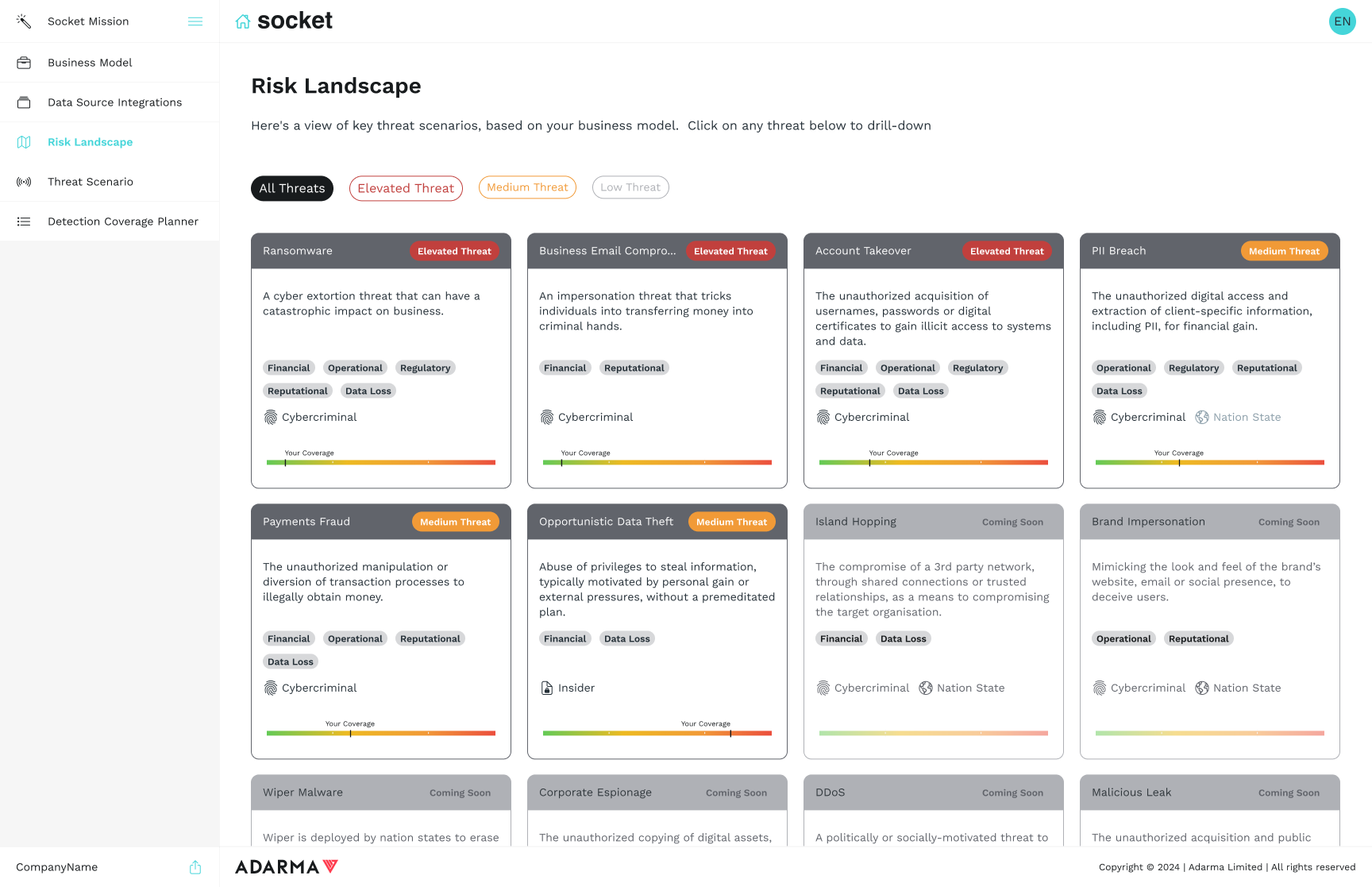
Explore Threat Scenarios
- View threat scenarios prioritised based on your business mission.
- Deep dive on any threat to explore risk factors and coverage.
Outcome
Understand in detail who threatens you and how.
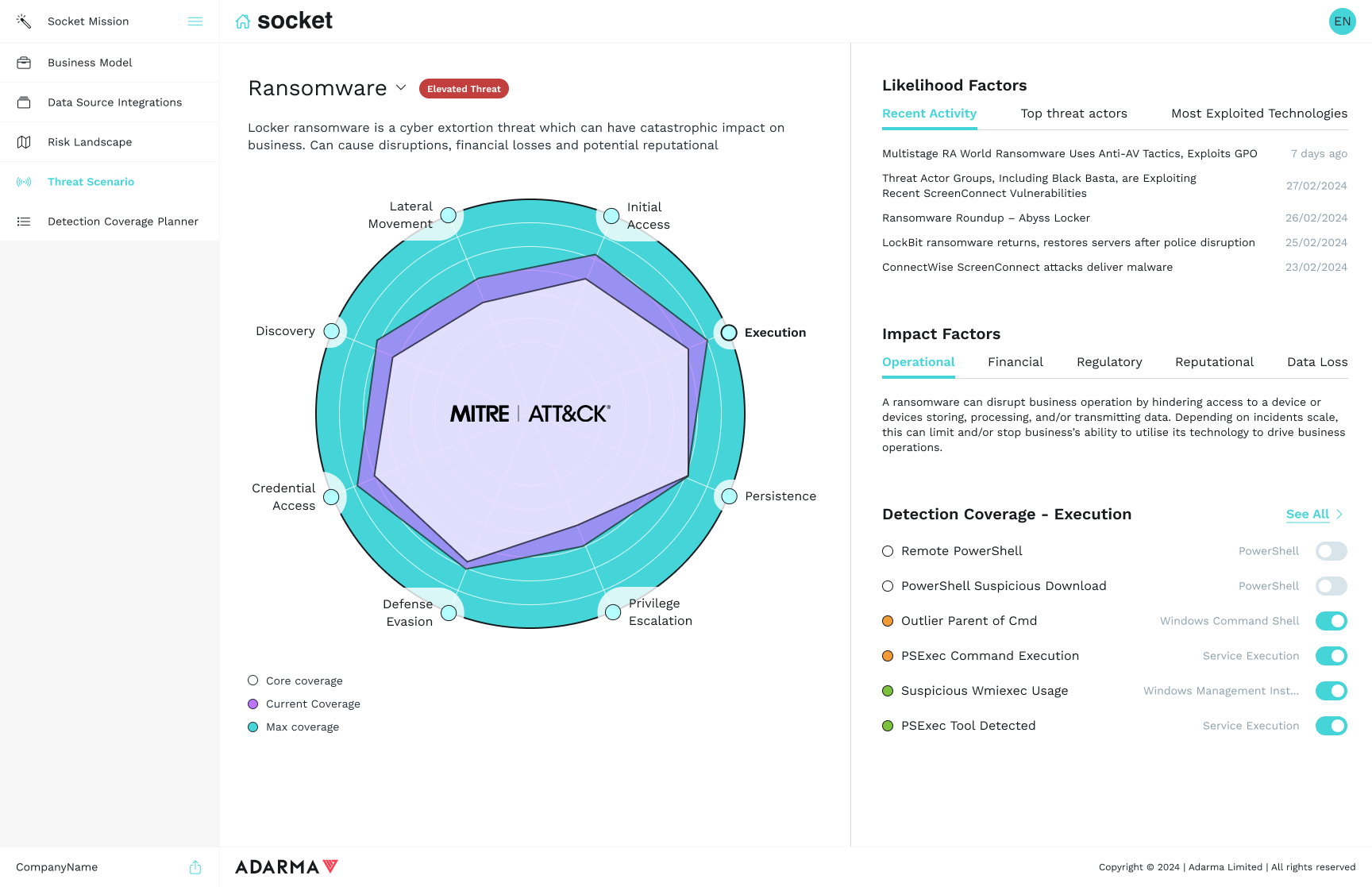
Explore Your Threat Model and Adjust Coverage
- Access insights into top threat actors and recent threat activities based on different scenarios.
- Identify the most exploited technologies within each scenario.
- Visualise any gaps or duplications in your coverage and determine how to optimise it accordingly.
- Deploy the necessary detection coverage to safeguard your organisation.
Outcome
Gain a comprehensive understanding of your readiness to defend against threats. Acquire visibility into your deployable controls, pinpoint any gaps, and receive guidance on how to effectively mitigate them.
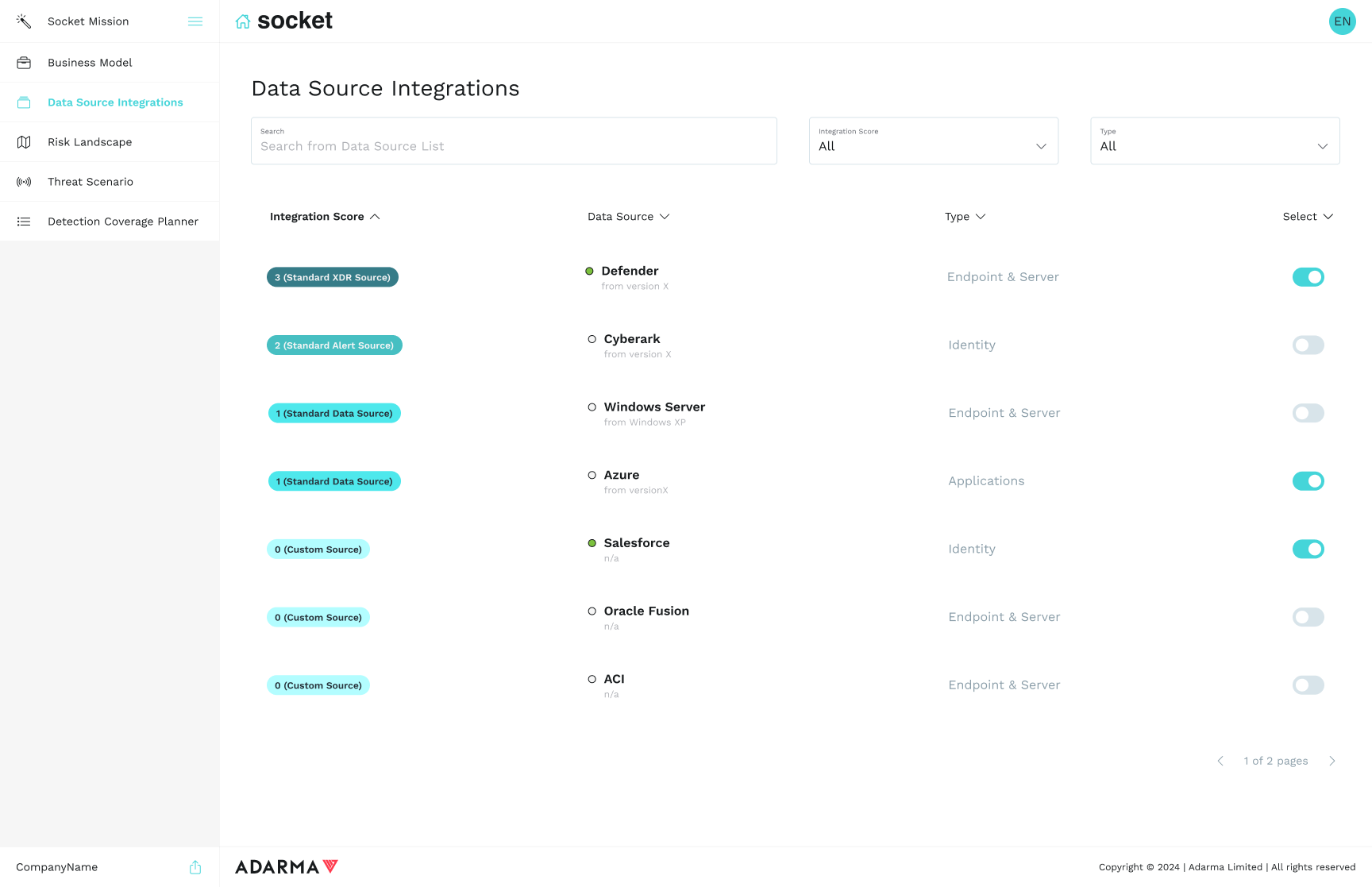
Integrate and Configure Data for Optimal Outcomes
Socket’s scalable architecture seamlessly connects your trusted tools, allowing you to:
- Integrate, configure, and customise any supported data source at no additional cost.
- Evaluate and select high-value data sources for integration, based on business context, data source quality, and threat coverage.
Outcome
Confidence that you are supplying your security operation with the right raw data to drive effective detections.
Ready to be proactive about your cybersecurity defences?
Socket empowers you to oversee threat coverage, reduce exposure, and quickly identify, investigate, and respond to threats efficiently and at scale.
Download the Report
How to Design a Future-Ready Security Operations Centre
Staying secure, adaptable, and agile in a rapidly evolving landscape where threats are constantly mutating requires more than just keeping up – it demands a proactive threat-led approach to cyber resilience.
Our latest report lays out a detailed blueprint for building a Security Operations Centre (SOC) that tackles today’s challenges while anticipating and preparing for tomorrow’s threats.

Partner Recognition
We have established strategic partnerships with market-leading security technology vendors. Our extensive investments in technology specialisation and training have made us one of the most highly qualified providers of our chosen technologies in the UK.














Book a Demo
Thank you. We will be in touch soon.
![adarma_logo_twgt-black[11615449]](https://adarma.com/wp-content/uploads/2022/10/adarma_logo_twgt-black11615449.png)









